Spotting a phishing (hacker) email
How to spot a phishing email
A phishing email is an email which looks legitimate but which tricks you into clicking a dangerous link or giving over your credentials to login to other systems like social media or banks.
Many people receive phishing emails. They are sometimes convincing.
General properties
- They look convincing
- You feel a sense of urgency to deal with the email due to the implied problem
- They do not actually come from the system in question even though they say they do
- Their email layout looks like the normal system email layout that you might get from the true system (e.g. your bank or facebook or whatever), but there are telltale signs that it is not from that system.
- They might have attachments, e.g. a fake bank statement, or fake password reset.
In this post I will show you a few mails, starting with a fake Facebook password reset email. If we look at the above, we will see how to (A) detect that it is not actually from the real system, and (B) how to spot that the content links are fake as well.
Don't panic
On items 1 and 2 above, don't panic. The key issue here is they create a sense of urgency. Your account, it says, has been hacked. Not true. In fact, until you click on links in this email, your account might well still be safe. FIRST check that the email is real. IF it is a fake email/phishing email, your account will only be hacked IF you comply with the email contents and click its links. In other words, it's possible that your account is in fact safe and it is you who will unlock it for hackers! So watch out.
A. Spotting that it is not from the real system
In general, the email "from" will say "Facebook" or your bank's name or similar. However, if you inspect the email address you will see it is not @facebook.com or @mybank.com or whatever. It will be something arbitrary or similar. So it might say @facebooksecurityz.com or @mybank.com.net or somesuch.
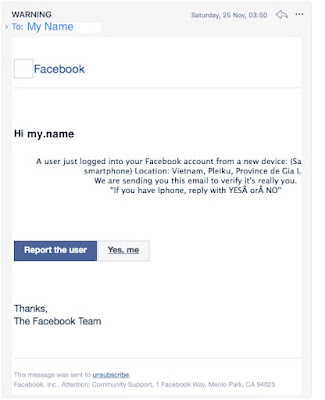
So if we look at this email message, we see a couple of warning flags. The first is that although it is addressed to you and it says it is from Facebook, we notice
(a) typographical errors, e.g. it says "If you have Iphone", not "If you have an iPhone". Presumably this is to trick you into revealing whether you have an iPhone or not so they can send targeted malware (viruses).
(b) It is addressed to you as "my.name", meaning they just took the front part (localpart) of your email address as your actual name. So if your email address was FatBoy123@gmail.com, it would say Hi FatBoy123. However, that's not your real name. Since Facebook and your bank have your REAL name, it would be addressed to your real name. Note the dot between my and name. That means that in this case, your email address was something like my.name@gmail.com.
Secondly if we click the from address, that is, who sent it to us, even though it says it is from Facebook, it is not:
Clearly that is not a Facebook address (yes this is actually a real hacker's address).
B. How to tell that the links are bad.
At the bottom of the email, it has two links - a fake report button, and a fake yes button. Both do the same thing actually - they take you to a dodgy website which asks you to login to facebook, or, they send your details to hacker email addressses. So, you do not click the link buttons, you rightclick them (or long-press on a phone or tablet). That will offer you the option to copy the link address.
When you open the web address separately in a browser, you'll see it is a fake login for Facebook. The entire page looks legitimate except the URL (web address). It is not legitimate. STOP NOW.